Data Protection Management System: Where to Start from
Data Protection Management System (DPMS) enables companies to integrate corporate governance and establish effective compliance and continually improve their data protection.
What Is a Data Protection Management System
A Data Protection Management System (DPMS) is a framework to enable companies to develop and establish an efficient data protection infrastructure. It provides them with systematic rules and regulations to cover policies, processes, and activities that involve personal data processing. DPMS has guidelines for the roles and responsibilities definition of the people in the company related to data protection. Having an effectively implemented DPMS helps organizations demonstrate compliance with data protection, maintain confidence and enhance trustful relationships with stakeholders, customers, and partners.
Key Components of a Data Protection Management System
“Implementation of a DMPS should start with an overview of current and related processes, then affected and responsible persons, and finish with defining the policy,” – states our partner expertree consulting.
What are the 2 challenges faced in data protection management? Data silos, lack of consolidated systems, dispersed data, and manual work are some of the issues companies need to find solutions for. Data protection management software is the key to resolving these challenges and enables organizations to set up effective and working data protection management.
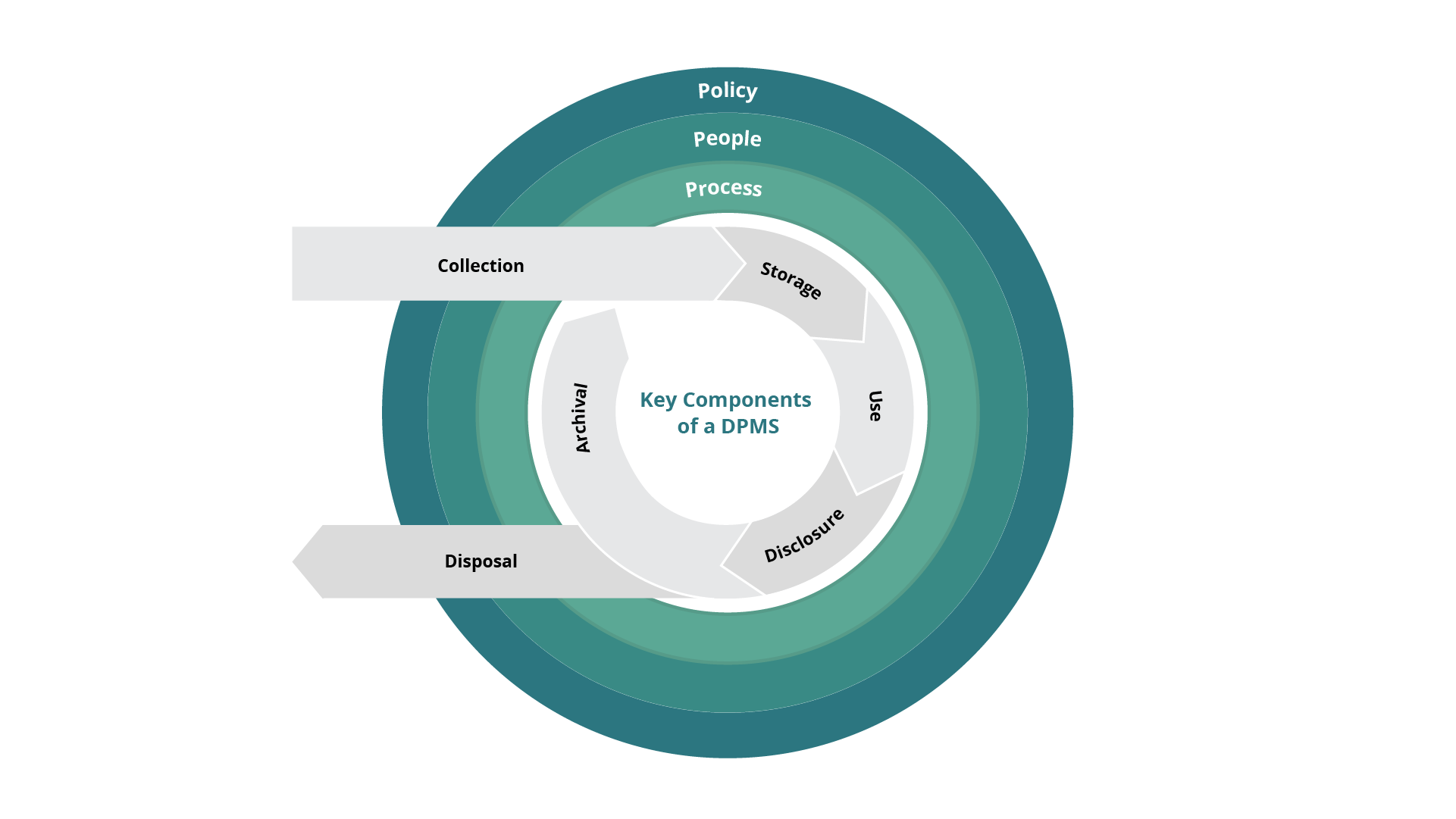
Process
For implementing a DPMS, organizations should start with getting an overview of current and related processes across the company.
Data lifecycle starts with collecting personal data to archiving/disposing of personal data) and goes across their business processes, systems, products or services. Moreover, companies must continuously control and revise the implementation of their data protection policies into processes organization-wide.
Here is a short guideline on maintaining all the processes in DPMS:
Process
1. Document personal data flows
Implementation
Use a data inventory map or data flow diagram.
Create a consent registry.
2. Incorporate data protection into business processes, systems, products, or services
Adopt a Data Protection by Design approach DPIA for systems or processes that are new or undergoing major changes.
Ensure compliance with the organization’s data protection policies.
Use contractual clauses
Conduct checks on compliance with clauses Establish a process for data breaches.
Use an incident record log to document incidents and post-breach responses.
3. Establish risk monitoring and reporting
Manage risk through an enterprise risk management framework with reporting mechanisms.
Conduct internal audits to monitor and evaluate the implementation of data protection policies and processes.
People
Senior Management must appoint at least one person to be the Data Protection Officer (DPO) responsible for all personal data protection-related matters and ensuring data privacy compliance.
Key responsibilities of a DPO:
- Ensures compliance through data protection policies and processes;
- Promotes a personal data protection culture and communicating personal data protection policies to stakeholders;
- Handles access and correction requests to personal data;
- Manages personal data protection-related queries and complaints;
- Alerts management about any risks that might arise with regard to the personal data handled by the organization.
Data Protection Policy
It is an integral part of corporate governance and must ensure strategic guidance on the implementation of the data protection framework.
What a DPP must include:
- Monitoring and managing personal data protection risks as part of corporate
governance - Maintaining Data Protection Impact Assessments (DPIA)
- Appointment of the DPO, CISO
- Establishing data protection training for employees
- Allocating resources for data protection, i.e., budget and manpower
- Providing instructions for managing data breaches, implementing of remediation plans, and handling of major complaints.
A checklist of questions for a DPMS
Policy
- What is the definition of personal data?
- What is the purpose of the policy?
- How often is this policy reviewed?
People
- Who is the intended audience of the policy?
- How does the policy apply? Are their roles and responsibilities clear and comprehensive?
- Who is the policy owner?
- Who verifies compliance and approves the policy?
Process
- Whose personal data is handled?
- What is the purpose of collecting personal data?
- What types of personal data are handled (e.g. name, NRIC, birth date, health details)?
- How are queries, feedback, disputes, and requests handled?
- Which third-party organization personal data is shared with if any?
- How does the company ensure that third-party vendors protect data?
- How are the data protection and Do-Not-Call provisions of the PDPA complied with throughout the data lifecycle?
- How is personal data protected?
- How should data incidents and data breaches be handled?
- When and on which systems or processes is DPIA conducted?
- How should policy exceptions be handled?
Review of Data Protection Policies and Practices
Companies should conduct regular reviews of their policies to eliminate the gaps and address them in time. To do so, the responsible people inside the organization need to monitor the changes within and outside the company, e.g., changes to regulations, best practices of DPMS, data incidents, new or altering processes, etc.
If any changes are observed, companies must revise their data protection policies and processes. Depending on the events observed, policies may require immediate or regular updates:
Ad-hoc changes: Major incidents (e.g., data leakage), legislative and regulatory amendments, and major changes inside the company (e.g., reorganization, merging, or acquisition).
Regular changes: Minor incidents (e.g. accidental unauthorized access by employee to personal data), revision of processes or systems that have minimal effect on data protection (e.g. change of DPO’s contact information).
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.

